These days, it seems like everyone is using a virtual private network (VPN) in order to bypass websites and keep their online activity private. But what are virtual private networks, and how do they operate?
Today, virtual private networks (VPNs) are practically associated with internet safety. By tunnelling your Internet traffic through an encrypted server, VPNs make it so that your credentials and other sensitive confidential information remain safe from inquisitive eyes. VPNs' ability to bypass censorship measures has made them useful for a variety of other tasks, such as private web surfing, secure file-sharing via torrenting, etc.
However, a virtual private network (VPN) entails more than just linking to a distant computer. Keep reading to find out more about virtual private networks (VPNs), how they operate, and what features you should search for in a VPN service.
What is VPN?
A virtual private network (VPN) is an intermediary that hides your true IP address from websites. Since your Internet protocol (IP) address is obscured, you can safely explore the web without worrying about your online activities being tracked back to you.
Virtual Private Network (VPN) functionality can be summarised by separating its component parts:
- Virtual Private Networks (VPNs) are so-called because they are provided in digital form. There is no cord or other accessory required.
- VPNs are "private" because they secure your link and prevent governments, ISPs, hackers, and others from monitoring your online activities.
- Virtual private networks (VPNs) establish an encrypted tunnel between your computer, the VPN server, and the public internet.
Types of VPN
Although virtual private networks have been used interchangeably throughout this piece, there is a wide variety of VPNs. These three are the most typical:
-
Client Based VPNs
When most people conceive of a VPN, they picture a client-based VPN. One can use a VPN application, software, or desktop driver to establish a secure connection between their local machine and a distant network. ExpressVPN, NordVPN, and StrongVPN are three of the most well-known client-based VPN services.
-
SSL VPNs
HTTPS VPNs are frequently used by businesses with mobile employees to provide users with secure, distant access to company networks from anywhere, including at home. In addition to safeguarding the company's network from strangers, these VPNs also enable employees to use their own personal devices to access the company's internal network.
-
Site to Site VPNs
Site-to-site VPNs encase LANs in a secure cocoon that can only be accessed by trusted, external networks. These virtual private networks (VPNs) are typically used by big corporations with numerous offices that require access to one another's internal networks.
Any number of local networks that share a connection to the Internet can be included in a site-to-site VPN (WAN).
How a VPN can help you protect your online Identity?
Using a virtual private network (VPN) can help protect your online identity by encrypting your online activity and hiding it from your internet service provider (ISP). When you browse the internet, the data you send or request, along with your IP address and destination IP address, first reaches your ISP. This means that your ISP can monitor and record all your internet activity.
However, when you use a VPN, your request first goes to the VPN server, where it is encrypted and then sent forward to the website you want to access. Your ISP is still present, but it won't be able to read your request or destination IP address because the VPN changes the IP address of your destination to a different IP address and encrypts it. Your ISP will assume that all your requests are going to the VPN's IP address, and it will forward all your requests to the VPN.
Once your request reaches the VPN server, it is decrypted, and the VPN forwards your request to the website you wish to access. The website or server will assume that the request is coming from the VPN server and allow the VPN to access the website, without revealing your true IP address or online activity to your ISP. Similarly, when you download a file, all the traffic flows from the web server to the VPN. The VPN encrypts all the information and then forwards it to your ISP, which still has no idea what's going on, as the information is encrypted. Finally, the information is forwarded to your device, decrypted, and displayed on your screen.
Using a VPN can help protect your online privacy and prevent your ISP from monitoring and recording your online activity.
Read also: 29 website speed statistics you should know
Is it Illegal to use a VPN?
Early in 2022, the use of virtual private networks (VPNs) became unlawful in a number of nations, including China, Iraq, North Korea, Russia, Turkey, Belarus, and Turkmenistan. Uganda, the UAE, and Oman are among the nations that impose partial bans on virtual private networks (VPNs).
However, VPN use is entirely lawful in many nations. This includes the USA, AU, UK, and NZ.
While virtual private networks (VPNs) are lawful in many countries, you still cannot use one to evade the law or hide your online activities. Virtual private networks (VPNs) are intended to make internet use more secure; they do not provide permission to engage in illegal activity online.
There's also the fact that VPN use might be against Hulu's and Netflix's ToS (Terms of Service). Streaming services may terminate your account or prevent you from using the service altogether if they discover that you are accessing the site via a virtual private network (VPN).
As using a virtual private network (VPN) circumvents the licencing arrangements streaming services have with content producers, the services have taken action to prevent its use. Due to the often-regional nature of these licencing arrangements, watching Netflix outside of your home nation may be a violation of Netflix's contract.
What Does a VPN do?
Virtual private networks (VPNs) are useful for more than just companies looking to safeguard proprietary information or tourists hoping to surf the web securely while in transit. Virtual private networks (VPNs) are useful for everyone who uses the internet, whether at home, in the office, or at school. Some of what a virtual private network (VPN) can do:
-
Hide Your Monitoring Behavior On the Internet
Both your Internet service provider and search engine use your browsing history to tailor their services to you, provide a more relevant experience based on where you are physically located, and ultimately profit from the information you provide them. Since VPNs mask your true IP address, search engines can no longer personally identify you while you're online.
If you're still signed into Google or Facebook, for example, they'll be able to see everything you do online unless you disable advertising monitors.
Even if you alter your Address, big businesses can still monitor you through methods like device tracking.
-
Remove Trackers and Spyware
In order to infiltrate users' machines with adware and monitoring devices like keyloggers, many hackers take advantage of unsecured public WiFi networks. Cybercriminals specifically capture data travelling between public sites and use it to identify and track down prospective victims.
When connecting to a server from your computer using a VPN software, all data sent between your computer and the server is encrypted. Complete data security from the moment it leaves your device to the moment it is decrypted is provided by this end-to-end encryption.
-
Data Encryption
All of your present Internet traffic is encrypted by a VPN programme. If you need to share any information or data that could be considered confidential, encrypting it will prevent governments and business agents from gaining access to it.
Benefits of Using
Why do so many people feel compelled to subscribe to a virtual private network? So, let's take a look at some of the advantages they offer.
-
Identity Fraud Protection
Theft of one's identity is becoming a major issue. Financial damages due to identity fraud rose by 42% in 2020, to $712.4 billion from $502.5 billion in 2019.
You can avoid having your personal information, banking details, and job history stolen by hackers by using a virtual private network (VPN) (like your address).
-
Price Inequality Stops
To tailor costs to your region, gender, and viewing patterns, many e-commerce sites use cookies to monitor your activity. Flights, literature, electronics, and lodgings are just some examples of the many categories vulnerable to price prejudice.
A virtual private network (VPN) can protect you from unfair pricing by hiding your online activity and location.
-
They're a strong defensive measure
Do you broadcast or play video games frequently? The easiest way to enjoy games without worrying about your link being disrupted by a DDoS assault is to use a virtual private network (VPN).
Your anonymity will be preserved if your true IP address remains hidden.
But a virtual private network protects only your device and network, not the server or provider. Download the "Site Security Reference Booklet" for helpful tips on keeping your website secure.
The avoidance of theft in online transactions relies on several factors, the first of which is a safe website.
-
They Make Homework Secure
When working online, VPNs allow you to connect to your company's network so you can view files and benefit from the same level of protection as in-office employees. VPNs allow you to bypass geographical restrictions by connecting to the internet through a remote computer. For example, some material on webpages, social media, and video-streaming services is limited based on the user's location.
-
They Unblock Online Filtering
You can use a virtual private network, or VPN, to gain access to content that may otherwise be banned by your institution, provider, or government. As these restrictions are typically implemented regionally or across an entire network, using a VPN to alter your virtual address allows you to avoid them.
How does a VPN work?
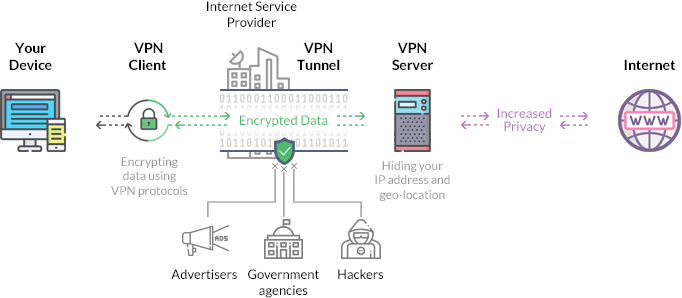
To begin using a virtual private network, you must first join up with a reliable VPN service and download and install their application or browser plugin.
This is how a virtual private network (VPN) protects your online privacy once you've joined.
Step 1: Connecting to a Virtual Private Network Host
To begin, you must activate the VPN by pressing the app's dedicated icon. By using this programme, your computer will establish a secure connection to a VPN server, which will then function as a go-between for your computer and the remote sites you access.
It's possible to access regionally-restricted material by connecting to a server in a specific nation or location with many VPN services.
Step 2: VPN Tunneling
Once you're linked to a VPN server, all of your traffic (both incoming and outgoing) will be encrypted before being sent through a secure "VPN channel." A virtual private network (VPN) tunnel is an encrypted channel through which a VPN server can communicate with other computers on your behalf.
When you visit a webpage or piece of content, your software decrypts the information and displays it to you.
Even though this information is protected, it still passes through your Internet service provider (ISP). Only traffic to and from the VPN server will be visible to your Provider. Most VPNs adhere to a "no trace" strategy and thus do not record your online activities.
It's important to remember that various VPNs employ varying security methods, so there is no single "correct" means to secure data. In 2023, the most widely used virtual private network types will likely be:
- OpenVPN
- Internet Key Exchange Version 2(IKEv2)
- PPTP
- Wiregaurd
- Layer 2Tunneling Protocol (L2TP)
Step 3: A Look at VPN Encryption, Encapsulation, and Decryption
If you use a virtual private network (VPN), the host will receive the information for you and secure it before you access the site or service. After that, it sends the protected info back to your device. The virtual private network software on your machine then decrypts the information for you.
To prevent your Provider from snooping on your online activities, many VPNs employ encryption to enclose user data in VPN-generated messages.
This may look like a lengthy procedure, but in reality it requires only a second or two. As you travel the web, your machine and VPN server will repeatedly go through these three steps. Given that VPNs operate invisibly, you might not even realise they are activated.
Imagine a delivery being sent through the postal; this is the most straightforward method to understand how a virtual private network (VPN) operates. After protecting the delivery with bubble film, you take it to the post office to have it delivered. The post office will verify the location before delivering it to the intended addressee. After it has been delivered, the item will be opened by the beneficiary, who will then put it to use.
In this image, the parcel depicts data that was downloaded from a server, the bubble wrap stands in for encryption, the post office stands in for the VPN connection, and the beneficiary is your personal computer along with the VPN software it uses.
Final Thoughts
It's undeniable that Proxies come with both benefits and drawbacks. They are used by businesses to safeguard their internal networks and sensitive data. You can use one to bypass filters and safeguard your online identity, privacy, and security. A virtual private network (VPN) offers added protection and benefits when used for legitimate purposes. You should always use a virtual private network (VPN), whether it's free or not, whenever you connect to an insecure network (public or private) or a website that you can't verify is secure. It's not a bad idea to use a free VPN service every once in a while, even though it's true that commercial VPNs have more benefits overall.



